We have the following logic to create a branch policy programmatically using Azure DevOps REST API.
$newPolicyBody = @{
type =@{
id = "{id}"
url = "{url}"
}
isBlocking = $true
isEnabled = $true
isEnterpriseManaged = $false
settings = @{
buildDefinitionId = "{buildDefinitionId}"
displayName = "Build Validation"
filenamePatterns = @("/{solutionName}/*")
manualQueueOnly = $false
queueOnSourceUpdateOnly = $false
validDuration = 0
scope = @{
repositoryId = "{repositoryId }"
refName = "refs/heads/{solutionName}"
matchKind = "Exact"
}
}
}
# API endpoint URL
$urlNewPolicy = "$orgUrl$solutionProjectName/_apis/policy/configurations?api-version=6.0"
try{
# Send a POST request to the API endpoint to create a new Policy
$newPolicyResponse = Invoke-RestMethod -Uri $urlNewPolicy -Method Post -Headers @{
Authorization = "$azdoAuthType $env:SYSTEM_ACCESSTOKEN"
"Content-Type" = "application/json"
} -Body $newPolicyBodyUpdated
}
catch {
}When executed above logic in a Azure DevOps pipeline we were getting “403 Forbidden error” error.
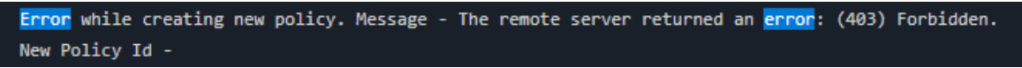
Let’s see what the issue was and how to fix it.
Reason and Fix:
The reason behind this issue was the introduction of a Prevention for unauthorized users to configure pipeline as a Build Policy in Azure DevOps in February 2024.
To resolve the issue, we need to grant additional permissions as shown below.
- Connect to your Azure DevOps project
- Go to Pipelines > Manage security
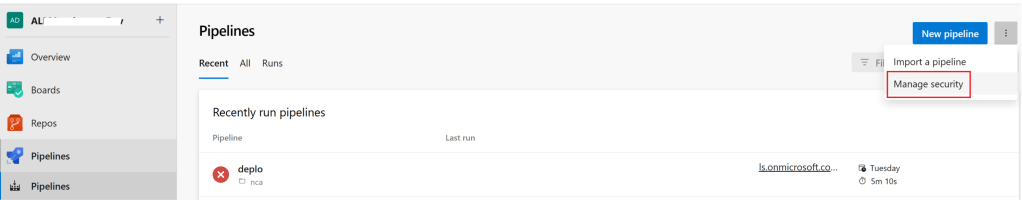
- Select Users > [Project Name] Build Service ([Organization Name]) and set the Queue builds to Allow.

- Re-run the pipeline should fix the issue.
🙂
![[Step by Step] Beginner : Create a PCF control and add it to a custom page](https://rajeevpentyala.com/wp-content/uploads/2024/12/image-49.png)
![[Step by Step] Configure and run 'Pipelines in Power Platform'](https://rajeevpentyala.com/wp-content/uploads/2024/08/image.png)

Leave a comment